
Crisis Response for Security Industry?
I spent a few days last week at the RSA 2015 conference, which brought together more than 30,000 professionals charged with the technology and policy strategies to keep your data safe.
I attended RSA to discuss Waggener’s data-driven approach to managing breach communications, which my colleague Nicole Miller presented to an audience of mostly corporate leaders. I left the conference struck by a hardening message to the public that breaches cannot be prevented but only be appropriately managed.
Which led me to ask, in the wake of unsettling cybersecurity events, does the security industry itself need crisis communications as much as corporations and governments?
One particular finding from Waggener Edstrom’s research reveals why the security narrative is so uncomfortable right now. News coverage and social conversation around a data breach is almost always negative, which is why in response you aim for the shortest news cycle possible. The optimal data breach cycle for a corporation is less than 75 days. Even if you can end your cycle in 60 days, two months is a long time for your customers, vendors, shareholders and employees to absorb negative headlines.
The security industry has it much worse than a 75 day news cycle. In 2014, major corporations and governments disclosed significant data breach news in January, February, March, May, June, July, August, September, October, November and December, and the drumbeat continued into 2015. The security industry itself is on track for a combined 500 day news cycle, a seemingly endless stream of bad news.
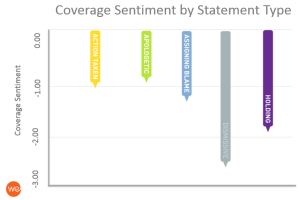
A second finding from the Waggener research showed how powerfully a company’s statements to the media impact the sentiment in post-breach coverage. Because breach coverage is so negative, a company or government’s goal should be to bring brand sentiment as close to neutral as possible.
Articles with statements that apologize to customers and focus on actions being taken show the best brand sentiment. In fact Waggener’s research shows that articles with spokesperson statements that dismiss a breach as impacting a small group of customers or say nothing about action or empathy, are twice as negative from a brand sentiment perspective.
Apologizing and agreeing to take action isn’t easy and it is particularly difficult to do when there may be wildly different ideas on where fault lies or which actions should be taken. We see that now with the debate raging over legislative approaches on information sharing. Despite a new normal defined by insecurity, the public and private sector still struggle to find common solutions that can re-balance the odds in favor of defense and against an attacker’s offense.
Communications is highly emotional and fear of the future discourages actions that feel risky. We often encounter leaders who want to believe that a situation will blow over and that doing nothing can be a strategic approach.
Waggener Edstrom’s research and the last fifteen months of security breaches proves that doing nothing during a prolonged crisis leads to worse outcomes.
One thing RSA made absolutely clear is that despite a crisis in confidence, today there is no lack of cash for the security industry. Corporations and governments cannot afford to skimp on security and there is explosive growth in the market, even if the solutions aren’t yielding perfect results.
As the RSA CEO Amit Yoran warned in his keynote RSA keynote Escaping Security’s Dark Ages, the industry is at an inflection point. This isn’t just a technology inflection point either. Without resolving the crisis in confidence and communicating actions being taken, the security industry could see a maddening amount of ongoing negative coverage and dramatic outcomes that change the industry landscape.
The latest blogs from WE
Decoding Gen Alpha: A Primer on the Next Gen of Consumers
Why Gen Alpha Will Fuel Spending This Season
Why Reputation Is a Business Driver in Healthcare

